By
Brian Krebs
Banks in Europe are warning about the emergence of a rare, virtually
invisible form of ATM skimmer involving a so-called “wiretapping” device that is
inserted through a tiny hole cut in the cash machine’s front. The hole is
covered up by a fake decal, and the thieves then use custom-made equipment to
attach the device to ATM’s internal card reader.
According to the
European ATM Security
Team (EAST), a nonprofit that represents banks in 29 countries, financial
institutions in two countries recently reported ATM attacks in which the card
data was compromised internally by “wire-tapping” or “eavesdropping” on the
customer transaction. The image below shows some criminal equipment used to
perpetrate these eavesdropping attacks.

Equipment used by crooks to conduct “eavesdropping” or
“wiretapping” attacks on ATMs. Source: EAST.
“The criminals cut a hole in the fascia around the card reader where the
decal is situated,” EAST described in a recent, non-public report. “A device is
then inserted and connected internally onto the card reader, and the hole
covered with a fake decal”
[pictured, bottom right].
Pictured above are what appear to be wires that are fed into the machine with
some custom-made rods. It looks like the data is collected by removing the
decal, fishing out the wire attached to the ATM’s card reader, and connecting it
to a handheld data storage device.
I sought clarification from EAST about how the device works. Most skimmers
are card slot overlay devices work by using a built-in component that reads the
account data off of the magnetic stripe when the customer inserts the card.
But
Lachlan Gunn, EAST’s executive director, suggested that
this device intercepts the card data from the legitimate card reader on the
inside of the ATM. He described the wiretapping device this way:
“It’s where a tap is attached to the pre-read head or read head of the card
reader,” Lachlan said. “The card data is then read through the tap. We still
classify it as skimming, but technically the magnetic stripe [on the
customer/victim’s card] is not directly skimmed as the data is intercepted.”
The
last report in my ATM skimming series showcased some major
innovations in so-called “insert skimmers,” card-skimming devices made to fix
snugly and invisibly inside the throat of the card acceptance slot. EAST’s new
report includes another, slightly more advanced, insert skimmer that’s being
called an “insert transmitter skimmer.”
Like the one pictured below, an insert transmitter skimmer is made up of two
steel plates and an internal battery that lasts approximately one to two weeks.
“They do not store data, but transmit it directly to a receiving device —
probably placed less than 1 meter from the ATM.

An insert transmitter skimmer. Source: EAST.
Both of these card skimming technologies rely on hidden cameras to steal
customer PIN codes. In a typical skimming attack involving devices that lay
directly on top of the card acceptance slot, the hidden camera is a pinhole spy
cam that is embedded inside the card slot overlay and angled toward the PIN pad.
Just as often, the camera is hidden in a false panel affixed directly above the
PIN pan with the pinhole pointed downward.
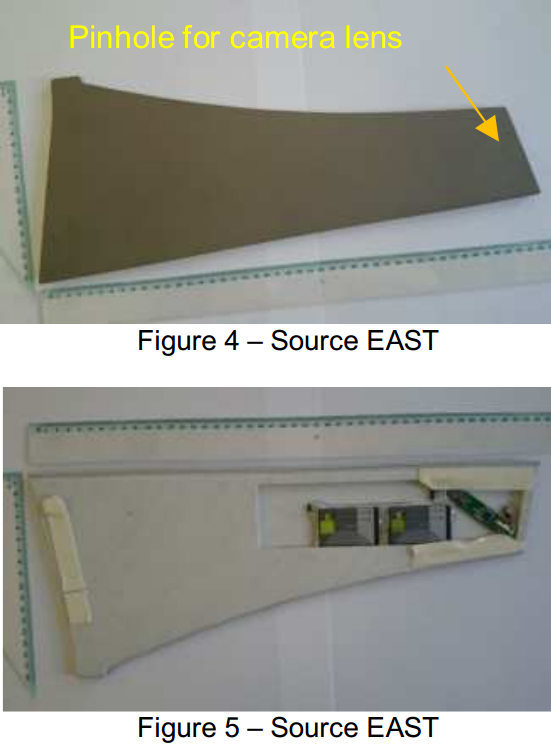
According to east, the use of false sidebar panels is becoming more prevalent
(see image below for an example). It is not unusual for hidden cameras to be
obscured inside of phony brochure racks as well.
As this and
other insert skimmer attacks show, it’s getting tougher to
spot ATM skimming devices. It’s best to focus instead on protecting your own
physical security while at the cash machine. If you visit an ATM that looks
strange, tampered with, or out of place, try to find another ATM. Use only
machines in public, well-lit areas, and avoid ATM's in secluded spots.
Last, but certainly not least, cover the PIN pad with your hand when entering
your PIN: That way, if even if the thieves somehow skim your card, there is less
chance that they will be able to snag your PIN as well. You’d be amazed at
how many people fail to take this basic precaution. Yes, there
is still a chance that thieves could use a PIN-pad overlay device to capture
your PIN, but in my experience these are far less common than hidden cameras
(and quite a bit more costly for thieves who aren’t making their own
skimmers).
Are you as fascinated by ATM skimmers as I am? Check
out my series on this topic,
All About
Skimmers.





